Xiao Qin's Research
SARTS: Security-Aware Real-Time Systems
This research is supported in part by the New Mexico Institute of Mining and Technology under Grant 103295 and by Intel Corporation under Grant 2005-04-070.
Improving quality of security is increasingly becoming an important issue in the design of real-time systems, which are indispensable for conducting business in government, industry, and academic organizations. This project addresses the issue of maximizing quality of security for real-time systems. We aim at developing and validating new mechanisms and schemes for security-aware real-time systems, including dynamic/static scheduling algorithms, security overhead modeling, security level controllers, and security-aware storage resources. These new schemes are expected to deliver high quality of security while meeting timing constraints of real-time systems. The novelty of the research comes not only from the security-aware schemes, but also from an improved methodology for designing and evaluating mechanisms and algorithms that integrate quality of security, scheduling, and resource management into real-time systems. Once the proposed schemes are adopted, our security-aware real-time scheduling algorithms and resource management mechanisms will be included within existing cyber security tools and services. Our solutions to the security-aware problem in the context of real-time systems include the following:
- Security-Aware Resource Management
- Security-Aware Scheduling on Clusters
- Security-Aware Task Allocation in Grids
- Security-Aware Scheduling for Embedded Real-Time Systems
- Adaptive Quality of Security Control in Storage Systems
- Fault Tolerance, Security, and Energy Issues in Real-Time Systems
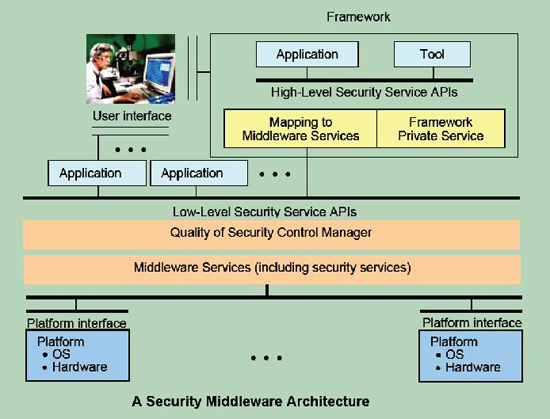
1.1 A Security Middleware Model. [Back to Top]
Recently, real-time applications with security requirements increasingly emerged in large-scale distributed systems such as Grids. However, the complexities and specialties of diverse security mechanisms dissuade users from employing existing security services for their applications. To effectively tackle this problem, in this paper we propose a security middleware (SMW) model from which security-sensitive real-time applications are enabled to exploit a variety of security services to enhance the trustworthy executions of the applications. A quality of security control manager (QSCM), a centerpiece of the SMW model, has been designed and implemented to achieve a flexible trade-off between overheads caused by security services and system performance, especially under situations where available resources are dynamically changing and insufficient. A security-aware scheduling mechanism, which plays an important role in QSCM, is capable of maximizing quality of security for real-time applications running in distributed systems as large-scale as Grids. Our empirical studies based on real world traces from a supercomputing center demonstratively show that the proposed model can significantly improve the performance of Grids in terms of both security and schedulability.
- 1.1.2 A Security Middleware Model for Real-time Applications on Grids. [ Abstract | PDF ]
T. Xie and X. Qin, IEICE Transactions on Information and Systems, Feb. 2006.
- 1.1.1 Towards a Security Service Integration Framework for Distributed Real-Time Systems. [ Abstract | PDF ]
T. Xie and X. Qin, Proc. 18th International Conference on Parallel and Distributed Computing Systems, Sept. 2005.
1.2 Dynamic Real-Time Scheduling with Security Awareness. [Back to Top]
An increasing number of real-time applications, such as aircraft control and medical electronics systems, require high quality of security to assure confidentiality, authenticity and integrity of information. However, most existing algorithms for scheduling independent tasks in real-time systems do not adequately consider security requirements of real-time tasks. In recognition of this problem we proposed a novel dynamic scheduling algorithm with security awareness, which is capable of achieving high quality of security for real-time tasks while improving resource utilization. We have conducted extensive simulation experiments to quantitatively evaluate the performance of our approach. Specifically, experimental results show that compared with three heuristic algorithms, the proposed algorithm can consistently improve overall system performance in terms of quality of security and system guarantee ratio under a wide range of workload characteristics.
- 1.2.3 Dynamic Task Scheduling with Security Awareness in Real-Time Systems. [ Abstract | PDF ]
T. Xie, X. Qin, A. H. Sung, M. Lin, and L. Yang, Int'l Journal of High Performance Computing and Networking, vol. 4, no. 3/4, 2006.
- 1.2.2 Open Issues and Challenges in Security-aware Real-Time Scheduling for Distributed Systems. [ Abstract | PDF ]
T. Xie, X. Qin, and M. Lin, Journal of Information, vol. 9, no. 2, March 2006.
- 1.2.1 Dynamic Task Scheduling with Security Awareness in Real-Time Systems. [ Abstract | PDF ]
T. Xie, A. H. Sung, and X. Qin, Proc. 19th International Parallel and Distributed Processing Symposium (IPDPS), 4th Int'l Workshop on Performance Modeling, Evaluation, and Optimization of Parallel and Distributed Systems, IEEE/ACM, April 2005.
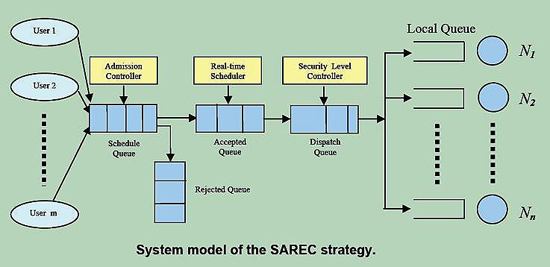
2.1 SAREC: Security-Aware Real-Time Scheduling for Clusters. [Back to Top]
Over the last ten years, clusters have become the fastest growing platforms in high-performance computing. Security requirements of security-critical real-time applications on clusters must be met in addition to satisfying timing constraints. However, conventional real-time scheduling algorithms ignore the applications’ security requirements. We investigated the problem of scheduling a set of independent real-time tasks running on clusters. In particular, we proposed a security overhead model that is capable of measuring security overheads incurred by security-critical tasks. Further, we proposed a security-aware scheduling strategy, or SAREC, which integrates security requirements into scheduling for real-time applications by employing our security overhead model. To evaluate the effectiveness of SAREC, we implement a security-aware real-time scheduling algorithm (SAREC-EDF), which incorporates the earliest deadline first (EDF) scheduling algorithm into SAREC. Extensive simulation experiments show that SAREC-EDF significantly improves overall system performance over three baseline scheduling algorithms (variations of EDF) by up to 72.55%.
- 2.1.3 Scheduling Security-Critical Real-Time Applications on Clusters.
T. Xie and X. Qin, IEEE Transactions on Computers, Vol. 55, No. 7, pp.864-879, July 2006.
- 2.1.2 Sharp: A New Real-Time Scheduling Algorithm to Improve Security of Parallel Applications on Heterogeneous Clusters. [ Abstract | PDF ]
T. Xie, X. Qin, and M. Nijim, Proc. 25th IEEE Int'l Performance Computing and Communications Conference (IPCCC), April 2006.
- 2.1.1 SAREC: A Security-Aware Scheduling Strategy for Real-Time Applications on Clusters. [ Abstract | PDF ]
T. Xie, X. Qin, and A. H. Sung, Proc. 34th International Conference on Parallel Processing (ICPP), pp.5-12, June 2005.
2.2 An Allocation Scheme for Parallel Applications with Security Constraints on Clusters. [Back to Top]
In this study, we address the issue of allocating tasks of parallel applications on clusters subject to timing and security constraints in addition to precedence relationships. A task allocation scheme, or TAPADS (Task Allocation for Parallel Applications with Deadline and Security Constraints), is developed to find an optimal allocation that maximizes quality of security and the probability of meeting deadlines for parallel applications. In addition, we proposed mathematical models to describe a system framework, parallel applications with deadline and security constraints, and security overheads. Experimental results show that TAPADS significantly improves the performance of clusters in terms of quality of security and schedulability over three existing allocation schemes.
- 2.2.1 A New Allocation Scheme for Parallel Applications with Deadline and Security Constraints on Clusters. [ Abstract | PDF ]
T. Xie and X. Qin, Proc. IEEE 7th International Conference on Cluster Computing (Cluster'05), Boston, Sept. 2005.
2.3 Security-Aware Real-Time Scheduling for Heterogeneous Clusters. [Back to Top]
This work characterizes the problem of improving quality of security for real-time parallel applications on heterogeneous clusters. We propose a new security- and heterogeneity-driven scheduling algorithm (SHARP for short), which strives to maximize the probability that parallel applications are executed in time without any risk of being attacked. Because of high security overhead in existing clusters, an important step in scheduling is to guarantee jobs' security requirements while minimizing overall execution times. The SHARP algorithm accounts for security constraints in addition to different processing capabilities of each node in a cluster. We introduce two novel performance metrics, degree of security deficiency and risk-free probability, to quantitatively measure quality of security provided by a heterogeneous cluster. Both security and performance of SHARP are compared with two well-known scheduling algorithms. Extensive experimental studies using real-world traces confirm that the proposed SHARP algorithm significantly improves security and performance of parallel applications on heterogeneous clusters.
- 2.3.2 SHARP: A New Real-Time Scheduling Algorithm to Improve Security of Parallel Applications on Heterogeneous Clusters. [ Abstract | PDF ]
T. Xie, X. Qin, and M. Nijim, Proc. 25th IEEE Int'l Performance Computing and Communications Conference (IPCCC), April 2006.
- 2.3.1 Incorporating Security into Real-Time Scheduling for Parallel Jobs on Clusters.
T. Xie and X. Qin, 26th IEEE Real-Time Systems Symposium (RTSS), Work-in-Progress Session, Dec. 2005.
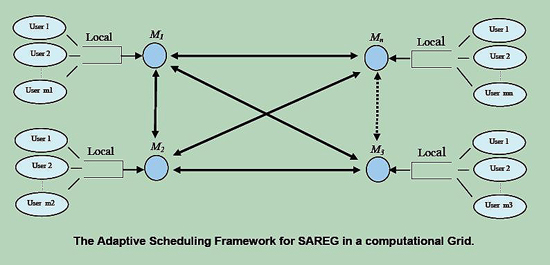
3.1 Enhancing Security of Real-Time Applications on Grids. [Back to Top]
Security sensitive real-time applications can take full advantage of a grid environment that allows grid participants to exercise a fine-grained control and allocation of computational resources. However, conventional real-time scheduling algorithms failed to fulfill the security requirements of real-time applications. In this research we proposed a dynamic real-time scheduling algorithm, or SAREG, which is able to enhance quality of security for real-time applications running on Grids. To make SAREG practical, we present a mathematical model to formally describe a scheduling framework, security-sensitive real-time applications, and security overheads. We leverage the model to measure security overheads incurred by an array of security services, including encryption, authentication, integrity check, etc. To evaluate the effectiveness of SAREG, we conducted extensive simulations using a real world trace from a supercomputing centre. Our experimental results show that SAREG significantly improves system performance in terms of quality of security and schedulability over three existing scheduling algorithms.
- 3.1.3. Performance Evaluation of a New Scheduling Algorithm for Distributed Systems with Security Heterogeneity. [Abstract | PDF]
T. Xie and X. Qin, Journal of Parallel and Distributed Computing, vol. 67, no. 10, pp. 1067-1081, October 2007.
- 3.1.2 A Security-Oriented Task Scheduler for Heterogeneous Distributed Systems. [ Abstract | PDF ]
T. Xie and X. Qin, Lecture Notes in Computer Science (LNCS 4297), pp. 35-46, ISBN: 978-3-540-68039-0, Springer-Verlag, Dec. 2006. Editors: Y. Roberts, M. Parashar, R. Badrinath, and V.K. Prasanna. (Proc. 13th Annual IEEE Int'l Conference on High Performance Computing (HiPC), Dec. 2006.)
- 3.1.1 Enhancing Security of Real-Time Applications on Grids through Dynamic Scheduling. [ Abstract | PDF ]
T. Xie and X. Qin, Lecture Notes in Computer Science (LNCS 3834), ISSN: 0302-9743, ISBN: 3-540-31024-X, Springer, August 2005, pp. 219-237, Editors: D. Feitelson, E. Frachtenberg, L. Rudolph and U. Schwiegelshohn. (Proc. the 11th Workshop on Job Scheduling Strategies for Parallel Processing (JSSPP), pp.146-158, Cambridge, MA, June 2005)
3.2 Security-Driven Scheduling for Data Grids. [Back to Top]
Security-sensitive applications that access and generate large data sets are emerging in various areas including bioinformatics and high energy physics. Data grids provide such data-intensive applications with a large virtual storage framework with unlimited power. However, conventional scheduling algorithms for data grids are unable to meet the security needs of data-intensive applications. In this paper we address the problem of scheduling data-intensive jobs on data grids subject to security constraints. Using a security- and data-aware technique, SAHA, a Security-Aware and Heterogeneity-Aware scheduling strategy, is proposed to improve quality of security for data-intensive applications running on data grids. To incorporate security into job scheduling, we introduce a new performance metric, degree of security deficiency, to quantitatively measure quality of security provided by a data grid. Results based on a real-world trace confirm that the proposed scheduling strategy significantly improves security and performance over four existing scheduling algorithms.
- 3.2.2. SAHA: A Scheduling Algorithm for Security-Sensitive Jobs on Data Grids. [ Abstract | PDF ]
T. Xie and X. Qin, Proc. IEEE/ACM 6th Int'l Symp. Cluster Computing and the Grid (CCGrid), 2nd Int'l Workshop on Cluster Security, May 2006.
- 3.2.1 Security-Driven Scheduling for Data-Intensive Applications on Grids. [Abstract | PDF]
T. Xie and X. Qin, Cluster Computing: The Journal of Networks, Software Tools and Applications, Special Issue: Evaluation and Optimization of High-Performance Computing and Networking Systems, Guest Editors: G.-Y Min and M. Ould-Khaoua, vol. 10, no. 2, pp. 145-153, June 2007.
4.1 Improving Security for Periodic Tasks in Embedded Systems. [Back to Top]
While many scheduling algorithms for periodic tasks ignore security requirements posed by sensitive applications and are consequently unable to perform properly in embedded systems with security constraints. In this paper we present an approach to scheduling periodic tasks in embedded systems subject to security and timing constraints. We design a necessary and sufficient feasibility check for a set of periodic tasks with security requirements. With the feasibility test in place, we propose a scheduling algorithm, or SASES (Security-Aware Scheduling for Embedded Systems), which accounts for both security and timing requirements. SASES judiciously distributes slack times among a variety of security services for a set of periodic tasks, thereby optimizing security for embedded systems without sacrificing schedulability. To demonstrate the effectiveness of SASES, we apply the proposed SASES to real world embedded systems such as an automated flight control system. We show through extensive simulations that SASES is able to maximize security for embedded systems while guaranteeing timeliness. In particular, SASES significantly improves security over three baseline algorithms by up to 107%.
- 4.1.2 Improving Security for Periodic Tasks in Embedded Systems through Scheduling.
T. Xie and X. Qin, ACM Transactions on Embedded Computing Systems, submitted May 2005. Accepted March 2006.
- 4.1.1 An Approach to Satisfying Security Needs of Periodic Tasks in High Performance Embedded Systems.
T. Xie, X. Qin, and A. H. Sung, 12th IEEE Int'l Conf. High Performance Computing (HiPC), poster session, Dec. 2005. (Refereed)
5. Adaptive Quality of Security Control in Storage Systems [Back to Top]
Power, security, and performance issues in modern storage systems are of critical importance. This work is intended to develop new adaptive strategies that can judiciously select appropriate power states and security services for disk I/O requests while endeavoring to guarantee various performance requirements (e.g., desired response times). In what follows, we describe our novel approaches to securing storage systems through adaptive strategies.

5.1 An Adaptive Write Scheme for Secure Local Disk Systems. [Back to Top]
Since security is of critical importance for modern storage systems, it is imperative to protect stored data from being tampered or disclosed. Although an increasing number of secure storage systems have been developed, there is no way to dynamically choose security services to meet disk requests' flexible security requirements. Furthermore, existing security techniques for disk systems are not suitable to guarantee desired response times of disk requests. We remedy this situation by proposing an adaptive strategy (referred to as AWARDS) that can judiciously select the most appropriate security service for each write request while endeavoring to guarantee the desired response times of all disk requests. Experimental results show that AWARDS significantly improves security and overall performance over an existing scheme by up to 325.0% and 358.9% (with averages of 199.5% and 213.4%).
- 5.1.2 Awards: An Adaptive Write Scheme for Secure Local Disk Systems. [ Abstract | PDF ]
M. Nijim, X. Qin, T. Xie, and M. Alghamdi, Proc. 25th IEEE Int'l Performance Computing and Communications Conference (IPCCC), April 2006.
- 5.1.1 Modeling and Improving Security of a Local Disk System for Write-Intensive Workloads. [Abstract | PDF]
M. Nijim, X. Qin, and T. Xie, ACM Transactions on Storage, vol. 2, no. 4, pp. 400-423, Nov. 2006.

5.2 Quality of Security Control in Parallel and Distributed Disk Systems. [Back to Top]
Parallel and distributed disk systems, which have been widely used in building networked and data intensive applications, are highly scalable and can alleviate the problem of disk I/O bottleneck. Although a number of parallel and distributed disk systems have been developed, the systems lack a means to optimize quality of security for dynamically changing networked environments. We remedy this situation by proposing an adaptive quality of security control scheme for parallel and distributed disk systems that makes it possible for disk systems to adapt to changing security requirements and workload conditions. Our approach is carried out in three phases: dynamic data partitioning, response time estimation, and adaptive security quality control. Hence, our scheme is conducive to adaptively and expeditiously determining security schemes for disk requests in a way to improve security of parallel and distributed disk systems while making an effort to guarantee desired response times of the requests.
- 5.2.5 Security-Aware Cache Management for Cluster Storage Systems.
M. Nijim, Z.-L. Zong, K. Bellam, X.-J. Ruan and X. Qin, Proc. the 17th Int'l Conf. Computer Communications and Networks (ICCCN), St. Thomas, Virgin Islands, Aug. 2008.
- 5.2.4 StReD : A Quality of Security Framework for Storage Resources in Data Grids. [Abstract | PDF]
M. Nijim, Z.-L. Zong, and X. Qin, Future Generation Computer Systems: The Int'l Journal of Grid Computing, vol. 23, no. 6, pp. 816-824, July 2007.
- 5.2.3 Adaptive Quality of Security Control in Networked Parallel Disk Systems. [ Abstract | PDF ]
M. Nijim, X. Qin, and T. Xie, Proc. 15th Int'l Conference on Computer Communications and Networks (ICCCN), Arlington, Virginia, Oct. 2006.
- 5.2.2 Sharp: A New Real-Time Scheduling Algorithm to Improve Security of Parallel Applications on Heterogeneous Clusters. [ Abstract | PDF ]
T. Xie, X. Qin, and M. Nijim, Proc. 25th IEEE Int'l Performance Computing and Communications Conference (IPCCC), April 2006.
- 5.2.1. An Adaptive Strategy for Secure Distributed Disk Systems.
M. Nijim, T. Xie, Z.-L. Zong, and X. Qin, NASA/IEEE Conference on Mass Storage Systems and Technologies, WiP Session, May 2006.
6. Fault Tolerance, Security, and Energy Issues in Real-Time Systems [Back to Top]
Fault tolerance, security, and energy issues in modern real-time systems are of critical importance. This work is intended to seamlessly integrate security services and energy conservation techniques for real-time systems while endeavoring to achieving high system reliability.
6.1 Security-Aware Fault-Tolerant Real-Time Systems. [Back to Top]
In the past five years, mandatory security requirements and fault tolerance have become critical criteria for most real-time systems. Although many conventional fault-tolerant or security approaches were investigated and applied to real-time systems, most existing schemes only addressed either security demands ignoring the fault-tolerant requirements or vice versa. To bridge this technology gap in real-time systems, in this study we propose a way of integrating fault recovery, confidentiality, and integrity services. The novel integration of security and fault recovery makes it possible to implement next-generation real-time systems with high reliability and quality of security.
- 6.1.2 Interplay of Security and Reliability using Non-Uniform Checkpoints. [Abstract | PDF]
K. Bellam, R. K. Vudata, X. Qin, Z.-L. Zong, M. Nijim, and X.-J. Ruan, Proc. 16th Int'l Conference on Computer Communications and Networks (ICCCN), Honolulu, Hawaii, Aug. 2007.
- 6.1.1 Integrating Fault Recovery and Quality of Security in Real-Time Systems. [Abstract | PDF]
K. Bellam, Z. Zong, M. Alghamdi, M. Nijim, and X. Qin, Proc. IEEE International Symposium on Ubisafe Computing, Ontario, Canada, May 2007.
Current Work
Current studies in this work include:
(1) Implement the proposed security-aware real-time scheduling schemes in a cluster.
(2) Conduct a rigorous testing experiment where the performance of a cluster with more than 1000 nodes will be evaluated.
(3) Develop a simulator to evaluate the performance of the security-aware scheduling schemes for large-scale clusters.
Updated on 5/29/2008