Solaris 2.X LPD home
This is the official home of Solaris2 lpd ported from 4.3BSD reno to native Solaris2.X (compiles on 2.3 - 2.6 cleanly with SPARCworks or gcc compilers.) To download the latest version of lpr/lpd click here. p5.07+ adds ms flag that understands stty commands, and enhanced -C option and filters. corrects the latest lpr/lpd overflow. I went through the code and audited the strcat, strcpy, sprintf functions that were in setuid code to make it more secure. See ChangeLog for complete details. Other things that this release of Solaris2 lpr/lpd fixes:
- BSD scandir re-written and implemented for Solaris/SYSV
- All BSD compatibility code removed - compiles native
- Fixed bug in baudrate that only allowed bauds up to 19200
- signals code replaced with posix sigaction
- wait3 replaced with wait and sigaction (as above)
- flock calls replaced with fcntl
- direct structured replaced with dirent
- S80lp contribution (slightly difference, but same functionality as lpr-p4)
- lpstat script rewritten in Perl
- lp script fixed to support more arguments
- p16 adds preemptive security check to eliminate remote hacks using sendmail arguments in config files (syslog AUTH|ALERT)
Some useful source code
 Click here for printer filters and utilities that are useful with
the lpd software shown above (and other printer spooling systems).
Click here for printer filters and utilities that are useful with
the lpd software shown above (and other printer spooling systems).
Tcl/Tk source code/executables
 If you have scotty/tnm (a Tcl/Tk
extension available
here)
hphubwatch
will provide you with a very nice tool to get all kinds
of useful information from HP Advance Stack SNMP capable hubs. Some of
the information available : port, frames, octets, media status, runts,
giants, media errors, alignment errors, total errors, port partitions,
port polarity jabbers, intruder alert status, frames per second, and
percentage of collisions to transmitted frames. It has already helped
us track down a bad 10Base-T cable, an overloaded subnet, and a port
that had reversed polarity. You can get it
here. To see a picture of this tool in action, click here.
If you have scotty/tnm (a Tcl/Tk
extension available
here)
hphubwatch
will provide you with a very nice tool to get all kinds
of useful information from HP Advance Stack SNMP capable hubs. Some of
the information available : port, frames, octets, media status, runts,
giants, media errors, alignment errors, total errors, port partitions,
port polarity jabbers, intruder alert status, frames per second, and
percentage of collisions to transmitted frames. It has already helped
us track down a bad 10Base-T cable, an overloaded subnet, and a port
that had reversed polarity. You can get it
here. To see a picture of this tool in action, click here.
 We use cpupie to monitor the performance of our servers. Any Unix
server that supports rstat will work with this tool. The
piecharts look like this:
We use cpupie to monitor the performance of our servers. Any Unix
server that supports rstat will work with this tool. The
piecharts look like this:
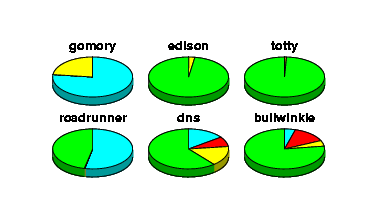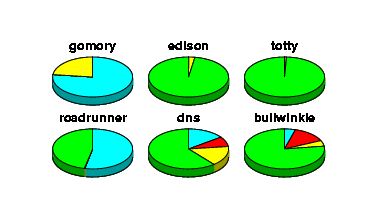
Instructions for usage and installation are included inside the executable (which is also a Tcl/Tk script) and with a README file. The output to printer resolution is better than what is displayed here because the application can output PostScript directly. There have been many speed improvements since the first release of this tool including removing the dependency on stoop and the external tkpiechart widget, and the inclusion of some of the math intensive calculations into a C library. It will also include labels indicating the actual percentages of CPU states if desired.
This program makes optional use of tclx and scotty/tnm.
A usenix paper discussing this and a few other visualization tools is available here tkvxvt (formerly ssa/Storage Array Visualization Tool)
is a Tcl (with TclX extensions) tool that I wrote to do some
visualization of our Sparc Storage Arrays. It breaks down disks by
subdisk and by plex and colors all subdisks in a plex with the same
color. It's primary purpose is to provide a tool to allow rearranging of
subdisks in a intuitive matter by showing where space is available and
letting you drag and drop subdisks from one disk to another. You can
also easily generate PostScript dumps of the entire storage array setup
by pressing the 'p' key and undo subdisk placements with the 'r' key.
A picture of this tool in action is available here
tkvxvt (formerly ssa/Storage Array Visualization Tool)
is a Tcl (with TclX extensions) tool that I wrote to do some
visualization of our Sparc Storage Arrays. It breaks down disks by
subdisk and by plex and colors all subdisks in a plex with the same
color. It's primary purpose is to provide a tool to allow rearranging of
subdisks in a intuitive matter by showing where space is available and
letting you drag and drop subdisks from one disk to another. You can
also easily generate PostScript dumps of the entire storage array setup
by pressing the 'p' key and undo subdisk placements with the 'r' key.
A picture of this tool in action is available here
The drag and drop is much improved. You can drag a subdisk to any empty region and it will beep if it won't work, or go there if it will. The multi-level undo code works well, and the command generation has been improved as of Aug '98.
 tklogger is a useful tool for watching logs created by syslog (or
other logging mechanism). No special files or interface to syslog are
needed because it works on plain text files and watches for updates to
the files specified.The type events watched is user configurable and
based either upon file type, pattern matching, or a mixture of the two.
The events are color coded. An extension allowing certain events to run
arbitrary scripts would be easily accomplished for the avid Tcl hacker.
Requires Tcl/tk (minimum 7.0/3.4) and TclX extensions. A sample startup
file is included in this.tkloggerrc file. To see what this tool looks like in action,
click here.
tklogger is a useful tool for watching logs created by syslog (or
other logging mechanism). No special files or interface to syslog are
needed because it works on plain text files and watches for updates to
the files specified.The type events watched is user configurable and
based either upon file type, pattern matching, or a mixture of the two.
The events are color coded. An extension allowing certain events to run
arbitrary scripts would be easily accomplished for the avid Tcl hacker.
Requires Tcl/tk (minimum 7.0/3.4) and TclX extensions. A sample startup
file is included in this.tkloggerrc file. To see what this tool looks like in action,
click here.
 X10 CP290 interface controller and explanation
X10 CP290 interface controller and explanation
Security and Intrusion Detection tools
 Here's a modification of rexec that I
call klaxon. Instead of actually executing anything, it returns a
benign error to the caller, and syslogs the calling host, username, and
name of attempted service access. It's also extremely useful for
detecting portscanner attacks like those perpetrated by ISS and
SATAN. Ident support (RFC931) is currently optional. klaxon is
useful in place of any tcp or udp service port where you would not
suspect activity. For Solaris2.X machines it will also work on the
rpc.rexd port. Examples follow.
Here's a modification of rexec that I
call klaxon. Instead of actually executing anything, it returns a
benign error to the caller, and syslogs the calling host, username, and
name of attempted service access. It's also extremely useful for
detecting portscanner attacks like those perpetrated by ISS and
SATAN. Ident support (RFC931) is currently optional. klaxon is
useful in place of any tcp or udp service port where you would not
suspect activity. For Solaris2.X machines it will also work on the
rpc.rexd port. Examples follow.
Compiling: extract tarfile and type make. Binaries appropriate for your OS will be built automatically. Check the README file for statically linking and ident information. example usage: add the following to /etc/inetd.conf and restart inetd (with kill -1) # # Local testing counterintelligence # rexec stream tcp nowait root /etc/local/klaxon klaxon rexec link stream tcp nowait root /etc/local/klaxon klaxon link supdup stream tcp nowait root /etc/local/klaxon klaxon supdup tcpmux stream tcp nowait root /etc/local/klaxon klaxon tcpmux rexd/1 tli rpc/tcp wait root /etc/local/klaxon klaxon rpc.rexd rje stream tcp nowait root /etc/local/klaxon klaxon rje tftp dgram udp wait root /etc/local/klaxon klaxon tftp
 As a companion to klaxon, I wrote tocsin . Tocsin logs port scan connections like klaxon, but does it on a per
network basis. You only need one tocsin process running per shared subnet.
Tocsin uses packet filters and runs out of the box on SunOS and Solaris
systems to catch port scanning attempts. Tocsin also differs in that it
is specifically designed to catch TCP SYN probe attempts. These are
probes that send a SYN packet to the target port. If it received a
response, there is a service there, if not, there is none. If it does
receive a response the normal procedure would be to acknowledge the
response and complete the 3 way handshake. However, the probes do not
acknowledge and are thereforece undetected by host-based daemon or
inetd software (such as klaxon). The README file gives more details and discusses
installation issues.
As a companion to klaxon, I wrote tocsin . Tocsin logs port scan connections like klaxon, but does it on a per
network basis. You only need one tocsin process running per shared subnet.
Tocsin uses packet filters and runs out of the box on SunOS and Solaris
systems to catch port scanning attempts. Tocsin also differs in that it
is specifically designed to catch TCP SYN probe attempts. These are
probes that send a SYN packet to the target port. If it received a
response, there is a service there, if not, there is none. If it does
receive a response the normal procedure would be to acknowledge the
response and complete the 3 way handshake. However, the probes do not
acknowledge and are thereforece undetected by host-based daemon or
inetd software (such as klaxon). The README file gives more details and discusses
installation issues.
All messages for tocsin and klaxon are logged at LOG_AUTH|LOG_NOTICE using syslog (similar to an su request.) There are two places in the source code that you should change if you want it logged with a different priority.
Kernel, Network, and Procfs source code
 juke.tar.gz is a device driver that was developed by modifying the
Solaris2 sst drivers as part of the SCSA packages put together by Patrick
Stirling. It provides a client program and kernel driver for Solaris
2.4 (portable to 2.3) that allows you to move tapes around in an Exabyte
10h or 10e jukebox. It is very useful for manipulating a tape jukebox
from within backup scripts.
juke.tar.gz is a device driver that was developed by modifying the
Solaris2 sst drivers as part of the SCSA packages put together by Patrick
Stirling. It provides a client program and kernel driver for Solaris
2.4 (portable to 2.3) that allows you to move tapes around in an Exabyte
10h or 10e jukebox. It is very useful for manipulating a tape jukebox
from within backup scripts.
 whozon (stand-alone version)
is sort of like the old Berkeley function of the same name.
This one is a lot more accurate (than standard w/who) on solaris because it
scans the proc table for open ttys and finds the userid associated.
The network-able client/server version for Solaris2 and SunOS
has a broadcast and all/hosts model for querying. It also doesn't rely
on Solaris' crappy utmp except to try to find out where somebody might
be logged in from.. This one is Accurate! It's also easily tcp-wrapperable
for those that use them. It requires a service to be added to /etc/inetd.conf
like
this:
whozon (stand-alone version)
is sort of like the old Berkeley function of the same name.
This one is a lot more accurate (than standard w/who) on solaris because it
scans the proc table for open ttys and finds the userid associated.
The network-able client/server version for Solaris2 and SunOS
has a broadcast and all/hosts model for querying. It also doesn't rely
on Solaris' crappy utmp except to try to find out where somebody might
be logged in from.. This one is Accurate! It's also easily tcp-wrapperable
for those that use them. It requires a service to be added to /etc/inetd.conf
like
this:
#
# Netwhod
#
netwho dgram udp wait root /usr/sbin/in.netwhod in.netwhod
 qps
is another Solaris2 utility that just gives you q quick process
listing of all processes on a machine. It supplies username, tty, proc name,
%cpu util, %mem util, and process_id. It's faster than ps because that's all
it does, and it only looks in procfs. It should be installed setuid root,
or run by root directly. All of the above supplied fields can be sorted
on with flags (in order referenced -u, -t, -n, -c, -m, -p).
qps
is another Solaris2 utility that just gives you q quick process
listing of all processes on a machine. It supplies username, tty, proc name,
%cpu util, %mem util, and process_id. It's faster than ps because that's all
it does, and it only looks in procfs. It should be installed setuid root,
or run by root directly. All of the above supplied fields can be sorted
on with flags (in order referenced -u, -t, -n, -c, -m, -p).
 The -a flag displays the first 80 chars of
process arguments (not my limit, part of procfs),
The -a flag displays the first 80 chars of
process arguments (not my limit, part of procfs),
 A useful set of tools nettools.tar.Z that will:
A useful set of tools nettools.tar.Z that will:
- show packets per second on an interface (Ethernet/fddi)
- break down packets per second by protocol type
- allow you to toggle between raw packets and % type utilization
Also included in nettools.tar.Z are nitroute, getroute, atalksnoop, and proxyarp.
These will:
- Show RIP packets by host
- Optionally timestamp packets
- Optionally show packets only from a certain host or netmask
- Optionally show packets dumped in hex format (raw)
- Works on NIT/DLPI, or in place of the router daemon on port 520
- Allow you to see just infinite routes (possible poison reverses)
- Dump and decode Appletalk packets showing protocol information
- Provide a proxy ARP implementation that runs on Solaris2 and used DLPI
 A program that forces users to pick
good passwords
that works on Windows (Samba), SunOS, and Solaris. It is web based,
uses Cracklib, and very restrictive.
A program that forces users to pick
good passwords
that works on Windows (Samba), SunOS, and Solaris. It is web based,
uses Cracklib, and very restrictive.
 gpw-dhh.c is a FIPS-181 style pronounceable random
password. This is a modification of the gpw program created by Thomas Van
Vleck. It includes a randomizer that takes 1-4 of the characters in the
password and converts them to upper case. It also takes a symbol from the set
of all numbers and symbols on the US ASCII keyboard and adds one randomly
at position 2 through positive 5 in the generated password. The possible
set of passwords is approximately 129 trillion words.
None of these will be dictionary words because of the insertion
of a random symbol somewhere in the middle.
gpw-dhh.c is a FIPS-181 style pronounceable random
password. This is a modification of the gpw program created by Thomas Van
Vleck. It includes a randomizer that takes 1-4 of the characters in the
password and converts them to upper case. It also takes a symbol from the set
of all numbers and symbols on the US ASCII keyboard and adds one randomly
at position 2 through positive 5 in the generated password. The possible
set of passwords is approximately 129 trillion words.
None of these will be dictionary words because of the insertion
of a random symbol somewhere in the middle.
Veritas Volume Manager tools
 Veritas Visualization Tool
(tkvxvt)
Veritas Visualization Tool
(tkvxvt)
 Here's a tool that will let you pack and condense VM disks that have
holes due to volume moves. It also will join grown subdisks that are non
adjacent for whatever reason.
Here's a tool that will let you pack and condense VM disks that have
holes due to volume moves. It also will join grown subdisks that are non
adjacent for whatever reason.
 vxrecreate
is a disaster recovery script. It constructs a simple
batch file that you can execute with the shell that has a bunch of vxassist
commands that you can use to make new volumes approximately the same size
as the originals on whatever new disks you have available. It rounds the
size up to the nearest 250MB increment. See this
ssa-managers mail-list
reference for more information.
vxrecreate
is a disaster recovery script. It constructs a simple
batch file that you can execute with the shell that has a bunch of vxassist
commands that you can use to make new volumes approximately the same size
as the originals on whatever new disks you have available. It rounds the
size up to the nearest 250MB increment. See this
ssa-managers mail-list
reference for more information.
Cyradm uses a few helper scripts to get it to do things like folder conversion.
The first is called splitmail. Splitmail is a (Taintperl) Perl script that scans through
the user's Unix style mailboxes in the ~/mail directory. It does several
things:
 Veritas tips and techniques pages.
There are lots of things here including deencapsulated rootdisk,
disaster recovery,
graphing ODM stats using Orca, etc.
Veritas tips and techniques pages.
There are lots of things here including deencapsulated rootdisk,
disaster recovery,
graphing ODM stats using Orca, etc.
Misc C Source code
 I have a collection of tools for parsing utmp and utmpx files including
ones that will split a utmp/utmpx file on a certain date, dump all
important records (something last doesn't do well), and eliminate a
certain user (e.g. ftp) from the file. There's also one that can be
run in an XDM xsession to properly update the wtmp/wtmpx files. Finally,
there's a program that will take a wtmp/wtmpx file and tell you if
it has any bad records (You can/should run this prior to splitting a file).
I have a collection of tools for parsing utmp and utmpx files including
ones that will split a utmp/utmpx file on a certain date, dump all
important records (something last doesn't do well), and eliminate a
certain user (e.g. ftp) from the file. There's also one that can be
run in an XDM xsession to properly update the wtmp/wtmpx files. Finally,
there's a program that will take a wtmp/wtmpx file and tell you if
it has any bad records (You can/should run this prior to splitting a file).
 We use the cyrus IMAP server. It's a wonderful product, but the administrative
tool is not conducive to converting mailboxes easily from old (e.g. BSD mbox
format) to new. I modified the cyradm utility and called it
cyradm_local.
You run it as the cyrus user on the imap server and it allows you to do such
things as create the user's mbox (creatembox), convert all of the user's
existing folders (createfolders), and delete a user's mailbox (deletembox).
These three procedures are all simple Tcl scripts (part of helper scripts
below) that are easy to follow.
Also, cyradm, when it starts checks for any files in the config directory
(hardcoded into cyradm.c as /etc/local/cyrus-scripts, but you can change it
and recompile) and sources them, dynamically adding any new procedures that
you define.
We use the cyrus IMAP server. It's a wonderful product, but the administrative
tool is not conducive to converting mailboxes easily from old (e.g. BSD mbox
format) to new. I modified the cyradm utility and called it
cyradm_local.
You run it as the cyrus user on the imap server and it allows you to do such
things as create the user's mbox (creatembox), convert all of the user's
existing folders (createfolders), and delete a user's mailbox (deletembox).
These three procedures are all simple Tcl scripts (part of helper scripts
below) that are easy to follow.
Also, cyradm, when it starts checks for any files in the config directory
(hardcoded into cyradm.c as /etc/local/cyrus-scripts, but you can change it
and recompile) and sources them, dynamically adding any new procedures that
you define.
Because there is a whole lot of setuid switching back and forth between real and effective userids (the user owning the mailboxes, and the cyrus user), output mailboxes sometimes end up with root permission. To solve this problem, when the conversion is all done and the folders are populated, the docyrus script is executed to make sure that all of the folders are actually owned by the cyrus user. This is a simple setuid Bourne shell script. If you don't use Solaris, and you're system cannot run setuid shells in a safe way (I used the -p flag in this script), you may want to write a small C program that does this instead. Splitmail can also be run by itself. Take a look at the source. Of most use is the -test argument. When given this argument followed by a username, splitmail will make sure that the user doesn't have any special .procmail recipes that may need special treatment, and it makes sure that all of the folder names don't have any special characters that would not be converted properly.
Additional notes
After the conversion is complete, the createfolders script invokes the cyrus reconstruct -r command on the user's main mailbox. I encourage you to look at the createfolders and creatembox scripts and modify them to suit your site. We have the user's main inbox on a striped+mirrored raid device and the user's folders in a RAID-5 device. We have also set it so that the user may not create folders under their inbox, but only in their 'folders' folder, hence the permissions that you see in the creatembox Tcl procedure.
Splitmail seems to work well enough, but don't treat it as production quality quite yet. Every once in a while I run into a strange quirk in somebody's mailbox that causes the conversion to abort of some reason. This is one reason why creatembox and createfolders are still separate procedures. Treat it as you would any beta software. It won't hurt anything, but it may fail every once in a while. If you find anything along these lines, please email me with patches (diff -c format preferred, thanks)
 pacct is a replacement for the pacct program
that compiles under SunOS and Solaris. It is much faster than the stock
versions. If you give it a number it only prints that number of records.
if you give it a negative number it prints that number of records from
the end of the pacct accounting file. (pacct is the program that
prints process accounting records if accounting is turned on)
pacct is a replacement for the pacct program
that compiles under SunOS and Solaris. It is much faster than the stock
versions. If you give it a number it only prints that number of records.
if you give it a negative number it prints that number of records from
the end of the pacct accounting file. (pacct is the program that
prints process accounting records if accounting is turned on)
 last is a replacement for the uility of the same name on Solaris2.X
machines. The version shipped with the OS has been unreliable. This
version is not as feature rich, but it does provide -n functionality,
where n is the number of entries to show.
last is a replacement for the uility of the same name on Solaris2.X
machines. The version shipped with the OS has been unreliable. This
version is not as feature rich, but it does provide -n functionality,
where n is the number of entries to show.
 A statically linked ls (gzipped tar) comes in very handy for
firewall based apps running in a chroot environment. This one is known
to run on Solaris2.X despite sun's insistence that static linking is not
supported. It includes stubs for dlopen, dlclose, and dlsym. It is
particularly useful for anonymous FTP setup.
A statically linked ls (gzipped tar) comes in very handy for
firewall based apps running in a chroot environment. This one is known
to run on Solaris2.X despite sun's insistence that static linking is not
supported. It includes stubs for dlopen, dlclose, and dlsym. It is
particularly useful for anonymous FTP setup.
 A good tool for servers with many
administrators, vi-lock replaces your standard editor (emacs, vi, whatever) with
one that locks the file with flock prior to opening it. This way you can
encapsulate all editors and ensure only one person at a time is editing
a system file.
A good tool for servers with many
administrators, vi-lock replaces your standard editor (emacs, vi, whatever) with
one that locks the file with flock prior to opening it. This way you can
encapsulate all editors and ensure only one person at a time is editing
a system file.
 Our APC SmartUPS v/s came with out the appropriate software to
drive it and properly shutdown the host after a time period when the
power went down. So, I wrote my own and constructed a cable as well.
Our APC SmartUPS v/s came with out the appropriate software to
drive it and properly shutdown the host after a time period when the
power went down. So, I wrote my own and constructed a cable as well.
 Here's my implementation of an inexpensive console server
Here's my implementation of an inexpensive console server
 Here's how we remotely turn the power on
and off for our servers using
X10 modules.
Here's how we remotely turn the power on
and off for our servers using
X10 modules.
 Here's a good way to do a paperless homework submission system using procmail
Here's a good way to do a paperless homework submission system using procmail

 More useful tools by Gary Mills at University of manitoba, CA
More useful tools by Gary Mills at University of manitoba, CA

mail me or visit my home page or visit the college's home page